Here you can find the basic information on how to carry out a “total-migration” from Windows Server to Zentyal Server. Please read carefully and test before applying this in production environment.
Note: Before starting with the migration, it is necessary to have Zentyal configured as an additional domain controller of a Windows Server.
Configure Zentyal as an additional domain controller
Thanks to the Samba integration, it is possible to make Zentyal an Additional Controller of an existing domain either by joining it to a Windows Server or to any Samba-based domain controller, like another Zentyal Server.
After having completed the domain join the LDAP, the DNS domain associated with Samba (local domain) and Kerberos information will be replicated transparently. Keep in mind that you need to take into account the following points before joining to another domain:
- Zentyal’s local LDAP data will be destroyed since it will be overwritten with the domain LDAP information
- Network time of the controllers has to be perfectly synced, preferably by using NTP
- When the users are synchronized from the other controller, Zentyal will create their associated /home/
directories. Check that these will not collide with the pre-existing home directories - All the controllers have to belong to the same domain
- DNS configuration is critical. Other domain controllers will try to push the information to the IP provided by your DNS system
If you have external IPs associated to your hostname (i.e. zentyal.zentyal-domain.lan), you may face synchronization problems if any of the controllers tries to use that IP to push data. Even if you have several internal IPs you may face the same problem because the DNS system performs ‘round-robin’ when answering DNS queries. If this is your case, you may want to uncomment sortlist = yes on the ‘/etc/zentyal/dns.conf’ file and restart the DNS server. This way the DNS system will always put the IP that matches the query netmask first.
Once you have checked all these points you can join to the domain from the Domain menu.
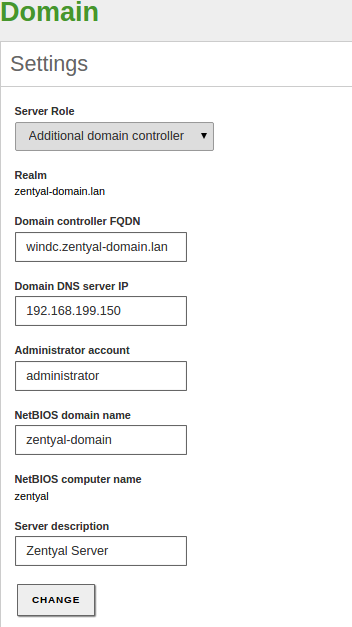
Saving the changes will take longer than usually because Samba will be provisioned and all the domain information replicated.
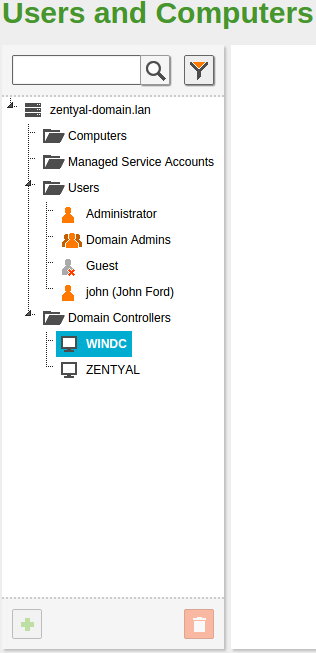
Exploring the LDAP tree from the Windows Server will also show the new domain controller.
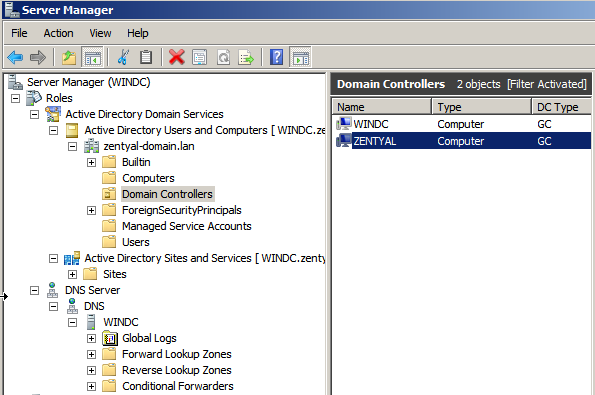
From now on LDAP, Samba local DNS domain and Kerberos information will be synchronized both ways. You can manage the LDAP information (users, groups, OUs, …) in any of the controllers and the information will be replicated to the other DCs. The process of joining to another Zentyal server is exactly the same.
Total migration
As mentioned above, all the domain controllers have the mentioned domain information. However there are some specific roles that belong to a specific server host, these are called FSMO roles or Operations Masters. Operation Masters are critical to the domain functioning. There are five FSMO roles:
- Schema master: LDAP schema master defines and pushes updates of the LDAP format
- Domain naming master: creates and deletes the domains of the forests
- Infrastructure master: provides domain-unique GUID, SID and DN IDs
- Relative ID Master: relative IDs assigned to the Security Principals
- PDC Emulator: compatibility with Windows 2000/2003 hosts, root time server
Using the Total Migration script you can transfer all these roles to a Zentyal server joined to the domain. From the /usr/share/zentyal-samba directory you execute:
administrator@zentyal:/usr/share/zentyal-samba$ sudo ./ad-migrate WARNING: This script will transfer all FSMO roles from the current owners to the local server. After all roles has been successfully transferred, you can shutdown the other domain controllers. Do you want to continue [Y/n]? Y Checking server mode... Checking if server is provisioned... Synchronizing sysvol share... syncing[SYSVOL] files and directories including ACLs, without DOS Attributes Transferring FSMO roles... Transferring Schema Master role from owner: CN=NTDS Settings,... Transferring Domain Naming Master role from owner: CN=NTDS Settings,... Transferring PDC Emulation Master role from owner: CN=NTDS Settings,... Transferring RID Allocation Master role from owner: CN=NTDS Settings,... Transferring Infrastructure Master role from owner: CN=NTDS Settings,... Migrated successfully!
From now on Zentyal is the only critical controller in the domain and all the features should continue working even if you turn off the others controllers, save scalability and network considerations.
Limitations
It’s important to check the list of current known limitations of Samba before planning your domain:
- Only one domain in the forest. Samba doesn’t support multiple domains or multiple forests
- Functional Domain level of the forest and the domain has to be min. 2003 R2, current max. 2008 R2
- Your hostname can not match your NETBIOS name. The NETBIOS name is generated using the left part of the domain. For example if your hostname is ‘zentyal’ your domain can not be ‘zentyal.lan’ but it could be ‘zentyal-domain.lan’
- Trust relationships between domains and forests are not supported
- GPOs will not be synced, but this can be workarounded manually following the official Samba documentation
- Users with non-ASCII names are not supported. (Accent marks, hyphen, special
characters, …)
