Amidst the ongoing shift to remote work due to the coronavirus pandemic, maintaining the security and efficiency of your Zentyal Server is paramount. This detailed guide aims to enhance your approach to Zentyal server monitoring, ensuring your infrastructure supports continuous, secure, and efficient operations.
Essential Login Monitoring for Security
Keeping track of who accesses your server is critical for maintaining security. Regularly monitoring both successful and failed login attempts helps ensure that only authorized users have access and helps to quickly spot any potential unauthorized access that could pose security threats.
- Successful SSH Logins: To check, use the command:
egrep "sshd\[.*\]: Accepted password for" /var/log/auth.log | wc -l
- Failed SSH Logins: To check, use the command:
egrep "sshd\[.*\]: Failed password for" /var/log/auth.log | wc -l
- Successful Zentyal Admin Panel Logins: To check, use the command:
grep 'check - Successfully authenticated user' /var/log/zentyal/zentyal.log | wc -l
- Failed Zentyal Admin Panel Logins: To check, use the command:
grep '_login - Failed login from:' /var/log/zentyal/zentyal.log | wc -l
Based on your monitoring results, consider implementing the following security measures to protect your Zentyal Server:
- Restrict Access: Ensure that only essential personnel have SSH and Zentyal GUI access. Review and disable any unnecessary use of the PAM (Pluggable Authentication Modules) option.
- Enhance Authentication: Verify that all users with SSH and GUI access employ robust passwords. Consider enhancing security further by replacing password authentication with certificate-based methods.
- Modify Default SSH Port: Change the default SSH port from 22 to an alternative port to reduce the risk of automated attacks and unauthorized access.
Also Check: Tips and Tricks to Keep Your Linux Server Running Smoothly
In-Depth Zentyal Server Status Monitoring
Leverage Zentyal’s Smart Admin feature to monitor server health comprehensively:
- Version Compatibility: Available directly in the GUI for commercial users or via a script for Development version users.
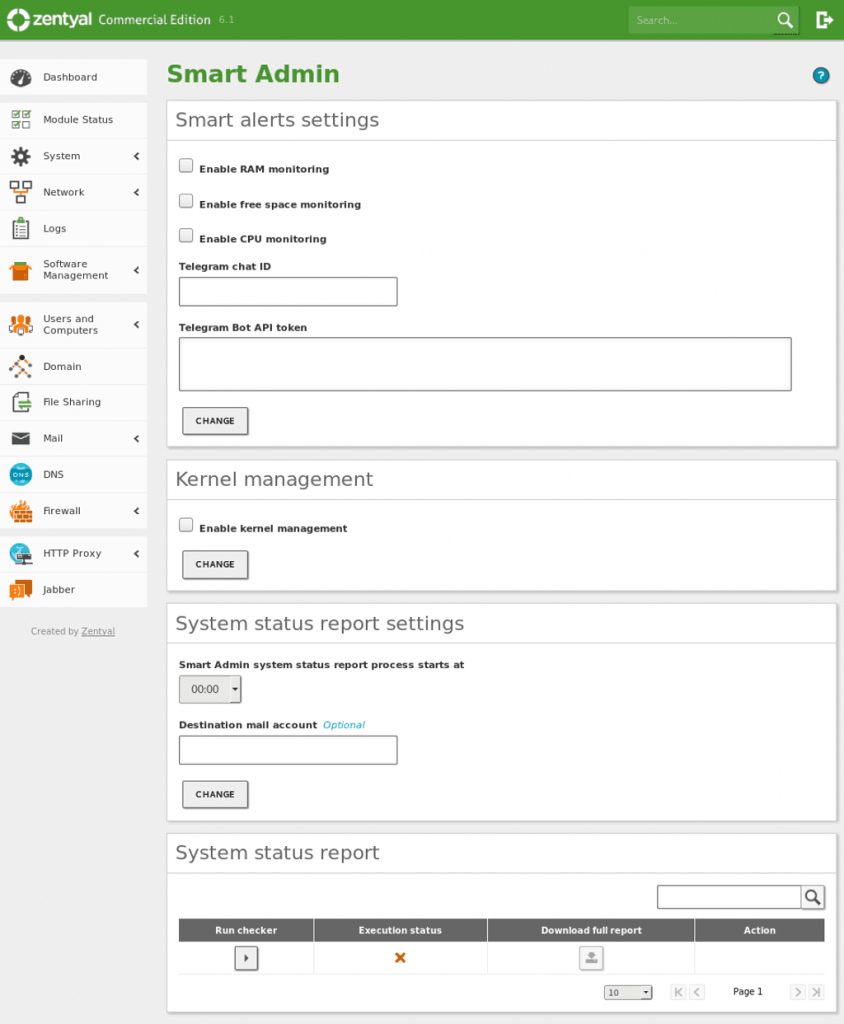
Zentyal Server Smart Admin GUI
- Monitoring Features Include:
- Alerts for crucial metrics like CPU, RAM, and disk usage to preempt issues.
- Management of outdated kernels.
- Comprehensive reports on Zentyal modules, system usage, pending updates, and error logs.
- Insights into domain controller activities and file-sharing services.
- Monitoring of email services managed through SMTP/POP3-IMAP4 modules.
Advanced Monitoring Techniques
According to the Zentyal documentation, it’s beneficial to integrate advanced monitoring techniques to gain deeper insights into your server’s performance and security:
- Network Traffic Monitoring: Use tools like nload, iftop, or iptraf to analyze incoming and outgoing traffic patterns and volumes.
- Resource Utilization: Regularly check system resource utilization to prevent overloads that could lead to server downtime. Utilize tools like vmstat and iostat for real-time system performance monitoring.
- Log File Analysis: Analyze log files with tools like logwatch or swatch. These tools help parse and simplify the process of reviewing detailed logs, making it easier to identify unusual activities or errors.
Setting Up Proactive Alerts
Configure proactive alerts to improve the management of your server resources effectively. Set up notifications to be delivered via email or to a designated Telegram group for issues such as unusually high CPU usage or critically low disk space, facilitating timely responses.
Further Resources and Support
For additional guidance, consult the Official Zentyal Documentation. This resource is crucial for an in-depth understanding of Zentyal server maintenance.
Contact for Support
If you encounter any challenges or have questions regarding your Zentyal Server monitoring setup, do not hesitate to reach out to our support team. We are dedicated to ensuring the continuous security and efficiency of your Zentyal Linux Server.

